Inside Cozy Bear, the shadowy Russian hacker group accused of hacking US agencies

To cybersecurity experts well versed in the dark arts of hacking, it will come as no surprise that the blame for a “global intrusion campaign” of cyber attacks on US government agencies has been pinned on a Russian group known as Cozy Bear.
With close links to the Kremlin’s foreign and domestic intelligence agencies, Cozy Bear, also known as ATP29, is among the world’s most infamous hacker groups, which over the past decade has been linked repeatedly with a string of high-profile attacks.
In 2015, it was implicated in an attack on the Pentagon that brought down the Joint Staff email system and its internet, while the following year it was widely blamed for an attack on the servers used by the Democratic National Committee.
Now, it has been reported that the group managed to break into US government systems by hacking into a widely used piece of software made by SolarWinds.
Burrowing into the networks through the IT software allowed the Russian hackers to quietly read government emails for months, giving them an immensely valuable look inside the workings of the US Treasury and US Commerce Department.
The SolarWinds hack also allowed the hackers to breach cybersecurity business FireEye, one of the most diligent businesses that had been tracking them. The hackers made away with FireEye's own hacking tools, a useful bonus from their attack on the US which lasted for months.
This latest hack is a classic example of a so-called "supply chain" hack. Even though the US government networks were secure, the Russian hackers still managed to sneak in by instead hacking into one of the businesses which supplies software to its target.
“APT29 has been successfully compromising systems now for over a decade across the globe,” says Tony Cole, chief technology officer at Attivo Networks. “The pandemic has given them a new and additional target to steal research.”
It was also blamed for the Oxford University and Imperial College hack on Covid-19 vaccine research in which experts believed it used “spear phishing” emails targeted at specific groups and specialist malware designed to quietly harvest data from an infected device or server.

But who is behind the organisation and what are its aims?
Back in 2014, Dutch security services caught a unique glimpse of the perpetrators. In an effort to investigate Russian hacking attempts, Dutch officials managed to break into the security camera system of a Moscow university building close to Red Square.
It was here, inside a computer lab in the university building, that Dutch security personnel got their first glimpse of the hacker now known as Cozy Bear as they were preparing to carry out an attack on the US government.
The Dutch security services had stumbled upon an intelligence jackpot: The university security cameras allowed them to peer over the shoulders of Russian hackers to watch their screens, and even to identify the members of the group.
These findings are backed up by expert analysis of the malware tools used by the hackers. One hacking tool used by the group, named Hammertoss, was found to only have been active during office hours in Moscow and Saint Petersburg.
Researchers have also found that the cyberattacks stopped during Russian national holidays, indicating that the hackers had been given time off work and left their malicious software dormant.
The Russian government has for years recruited thousands of promising young computer programmers who could use their expertise for hacking into computer systems in other countries.
In 2014, Cozy Bear hackers broke into an American research organisation. They spread a video titled “Office Monkeys LOL Video.zip” which appeared to be an innocent-looking video of monkeys wearing shirts and ties. When amused employees of the organisation shared the video, in the background the file actually spread malware inside networks that gave hackers access to secret files.
Cozy Bear was also involved in the 2016 hack of the US Democratic National Committee. Cozy Bear hackers had sat on the private network for over a year, but were unaware that a rival Russian government hacking group, Fancy Bear, had also broken into the servers in search of valuable data.
And in 2017, the Cozy Bear and Fancy Bear groups launched attempts to steal secret files from Dutch government departments. The hackers were particularly interested in the country’s upcoming general election, and the hacking attacks forced the Dutch government to count votes by hand to avoid the risk of election interference.
What techniques do they use?
The group has an arsenal of cyber tactics at its disposal to exploit vulnerable people. Its basic strategy typically involves initially casting a net far out into the internet with thousands of emails designed to lure in unsuspecting people online.
In a tactic known as “spear phishing”, it poses as a trusted sender of a company or organisation that a person might be a customer of, for example. The aim is to deceive them and make the target think the email is legitimate. It's a simple but effective trick that often forces users into sharing credit card details, passport information and more.
According to the National Cyber Security Centre (NCSC), the group targets what’s known as “publicly available exploits” in the early stages of its attacks. In practical terms, that means software and hardware that has seen increasing use since the start of lockdown as millions of people have been forced to work from home.
“They're using known vulnerabilities in some Citrix equipment and other firewalls and routers and things like that and exploiting those to get into the network,” says Professor Alan Woodward, computer scientist at the University of Surrey.
The broad targeting “potentially gives the group access to a large number of systems globally” as part of its initial grab for log-ins and other sensitive credentials.
Once these systems of global interest are compromised through its initial strategy, it can make more targeted attacks with its roster of sophisticated malware too.
One type of malware, known as “SoreFang” among security officials at the NCSC, latches onto HTTP code typically carrying internet traffic in and out of IT systems to extract information from victims.
Another set of custom-made malware, known as WellMess or WellMail, has been in use since at least 2018, that employs computer code to upload and download files in a compromised system at will.
WellMess is a piece of software used by the Russian hackers that security experts have seen being used since it was first found on the computer networks of Japanese companies in 2018.
Hackers place the WellMess software on a target computer network to act as a portal to smuggle out stolen documents. They can also use WellMess to transfer new instructions into their malicious software, helping them to change which networks are targeted and which files are sneaked out.
WellMail is another piece of malicious software which hackers can plant on to computer systems to smuggle commands on to computer systems and then to remove data from networks.
The software, which has never publicly been named or examined before the revelation of the Russian hacks on coronavirus research, sends hackers information on the username of whoever is logged in to a computer.
Have they been successful?
It is still unknown who is behind the attack on US government agencies, although the Washington Post reported that the Russian hacking group known as Cozy Bear, or APT 29, was behind the campaign.
What’s clear is that the group has been successful in the past, breaking into research organisations and government systems alike.
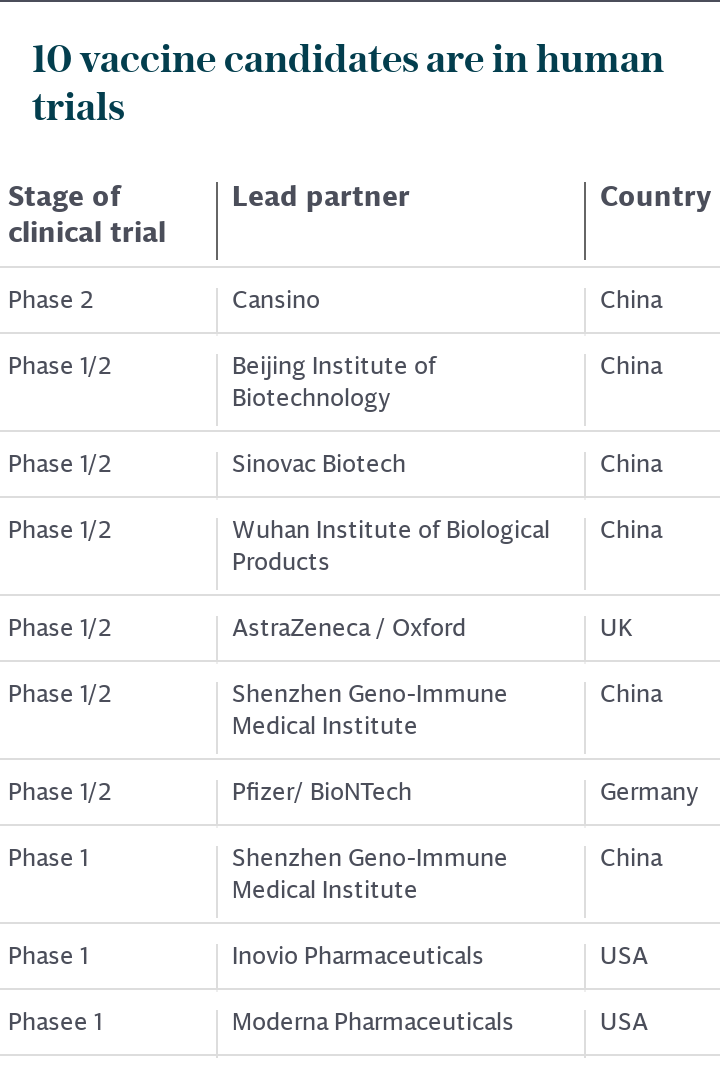
In May, the NCSC issued a public warning about top level hackers eyeing up vaccine researchers in an attempt to steal critical information from them.
Healthcare workers and researchers were urged to change their passwords to avoid being caught up in so-called “password spraying” strategies that see hackers attempt to use commonly-used passwords for the log-ins of staff at organisations with prized information.

 Yahoo Finance
Yahoo Finance 