Insurers 'funding organised crime' by paying ransomware claims
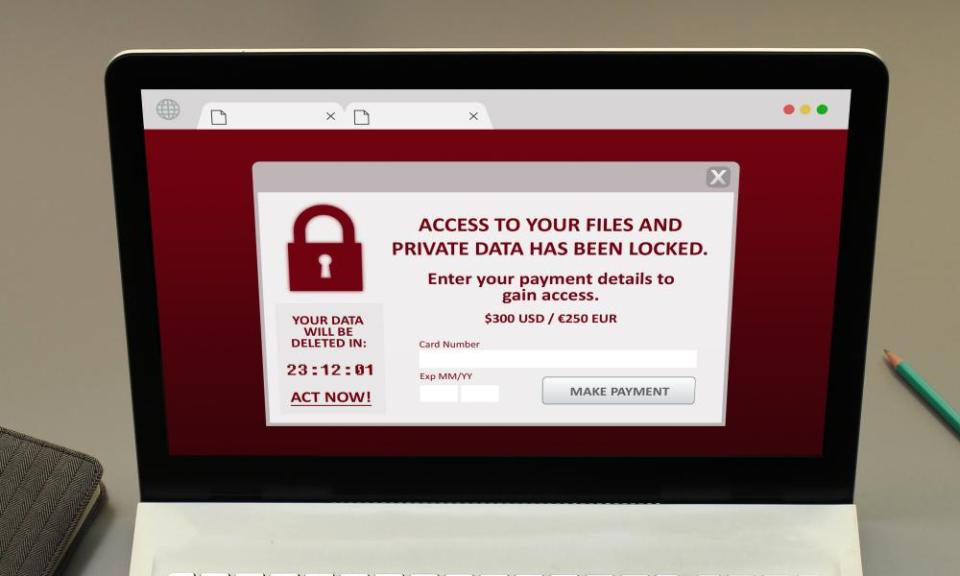
Insurers are inadvertently funding organised crime by paying out claims from companies who have paid ransoms to regain access to data and systems after a hacking attack, Britain’s former top cybersecurity official has warned.
Ciaran Martin, who ran the National Cyber Security Centre until last August, said he feared that so-called ransomware was “close to getting out of control” and that there was a risk that NHS systems could be hit during the pandemic.
The problem, he said, is being fuelled because there is no legal barrier to companies paying ransoms to cyber gangs – typically from Russia and some other former Soviet states – and claiming back on insurance. “People are paying bitcoin to criminals and claiming back cash,” Martin said.
“I see this as so avoidable. At the moment, companies have incentives to pay ransoms to make sure this all goes away,” the former intelligence chief said. “You have to look seriously about changing the law on insurance and banning these payments, or at the very least, having a major consultation with the industry”.
Britain’s extortion laws prohibit the payment of ransoms to terrorists, and were drawn up largely in response to the threat of kidnapping. But cyber-attacks are not carried out by terror groups, and so there is no bar to paying ransom demands – and it is possible to make an insurance claim if no personal data was involved.
Criminal hacking groups tend to be based in Russia and former Soviet states outside the Baltic region, Martin said, operating while the Kremlin and other governments in the region turn a blind eye to their activities.
Some groups claim they have made so much money they are publicly announcing their “retirement” on line, while the Wizard Spider or RYUK gang is estimated to have made $150m from online extortion according to a study of bitcoin transactions.
So called ransomware attacks involve groups hacking into and seizing control of corporate data systems. The gangs demand money – typically up to $10m a time – to give back access to the systems. “Attackers often set great store in being reliable once you have paid them, providing testimony from involuntary customers,” Martin said.
Travelex, a UK-based provider of foreign exchange services, paid $2.3m last year to regain control after hackers shut down its networks, but the company subsequently fell into administration and had to be restructured with the loss of 1,300 jobs. Smartwatch maker Garmin also reportedly paid to recover files, after suffering a crippling attack last summer.
Criminal attackers say they will not target hospitals or health centres, believing that such an attack would have wider diplomatic repercussions. But Martin said the worry is that IT systems do not readily identify themselves online, so a mistaken attack with wider consequences remains possible.
In 2017, NHS systems were among those seriously disrupted by the WannaCry attack, which emerged from North Korea. Although not a ransomware attack, the disruption caused to hospital systems demonstrates how serious the health sector could be affected in the UK and elsewhere.
German police launched an investigation in September after a woman died during a cyber-attack on a hospital in Dusseldorf. Doctors had been attempting to transfer the patient to another facility 30km away.
Other recent ransomware attacks have been conducted against EuroFins, a Belgian company that provides forensic services and disrupted police investigations in England and Wales, and elsewhere for some months although this was not widely reported at the time. It too reportedly paid a ransom.
Gangs often scout their targets and will tailor their demands to the size of the customer – there are even examples of small businesses such as hairdressers being targeted and payments of £1,500 being demanded.
Companies who have effective backups and can otherwise shrug off a hacker attack also find themselves under pressure to pay, because gangs are now threatening to leak stolen data online, an evolution of the classic ransomware model.
Martin said it was difficult to track the level of ransomware activity, because there was a lack of disclosure obligations, unless personal data is involved. But he added that he regretted not being able to change the law during his time in government and action was needed soon.
“In the last year, experts are saying this is close to getting out of control,” the former intelligence agency chief said. “The law is nobody’s fault, it was written for another purpose, but it has become OK to pay out to criminals”.

 Yahoo Finance
Yahoo Finance 