IoT IAM Market by Component, Security Type, Deployment Mode, Organization Size, Vertical and Region - Global Forecast to 2027

Global IoT IAM Market
Dublin, July 15, 2022 (GLOBE NEWSWIRE) -- The "Global IoT IAM Market by Component (Solutions and Services), Security Type (Network Security, Endpoint Security, Application Security, and Cloud Security), Deployment Mode, Organization Size, Vertical and Region - Forecast to 2027" report has been added to ResearchAndMarkets.com's offering.
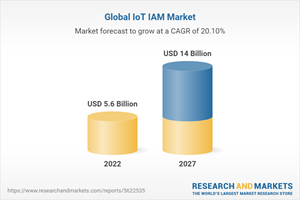
The global IoT IAM market size is expected to grow from USD 5.6 billion in 2022 to USD 14.0 billion by 2027, at a Compound Annual Growth Rate (CAGR) of 20.1% during the forecast period.
With the rapid and widespread adoption of IoT devices, practically every industry sector is exposed to IoT botnet-based cybersecurity threats. Therefore, organizations across the globe are adopting IoT security and deploying advanced IAM solutions to safeguard their connected computing and personal devices.
COVID-19 has been one of the biggest global challenges of the current generation. The ongoing projects were paused due to a decline in the budgets. The projects, which were highly strategic initiatives and projects involving technologies directly linked to COVID-19, were not put on hold. New trends emerge such as work from home infrastructure, collaboration tools, virtualization infrastructure, VPN networking, mobile devices, security and desktop support. Due to BYOD and virtual working trends, there was a high rise in cyberattacks.
The increase in cyberattacks and new vulnerabilities is leading organizations worldwide to rethink their security setups. To manage employees working from home, companies rely extensively on remote-based monitoring of the workforce, enhancing the demand for IoT solutions. This helps bring transparency, provide real-time tracking, improve safety, and ensure meeting government compliance. However, the cybersecurity of remote workforce and enterprises plays a vital role in catering to their clients during lockdowns. Therefore, it offers opportunities for the IoT identity and access management market.
The small and medium sized enterprises are estimated to account higher CAGR during the forecast period
SMEs are increasingly investing in the Internet of things (IoT) to gain a competitive edge. Instead of full-scale investment in IoT, SMEs opt for secure and stable IoT platforms. These platforms facilitate these SMEs to overcome technical challenges without having to solve them internally.
Also, to protect IoT applications and networking devices from unauthorized access, vulnerabilities, and attacks, SMEs opt for IAM solutions. Cybercriminals intend to benefit from the poor security in this segment by using the automation technique to attack many applications at a time. Hence to protect data and integrity and user confidential information, SMEs are opting for IAM solutions.
Among regions, APAC to hold a higher CAGR during the forecast period
The growth of the IoT IAM market in APAC is highly driven by technological advancement across the region. China is anticipated to be the leading country for IoT IAM Market growth in Asia Pacific, followed by Japan. IoT IAM market continues to grow steadily across multiple industries like transportation, retail, manufacturing, resources, and utilities driven by the increased capacity and reliability of fiber and cellular network infrastructure.
The increased focus on building smart infrastructures such as wider connectivity coverage, 5G deployment, public wi-fi zones, smart grid, and initiatives like smart cities, Industry 4.0, and special economic zones are the main driving factors for the IoT IAM market growth in the countries across Asia Pacific region.
Key Topics Covered:
1 Introduction
2 Research Methodology
3 Executive Summary
4 Premium Insights
4.1 IoT IAM Market Overview
4.2 IoT IAM Market Share of Top Three Verticals and Solution, 2022
4.3 Geographical Snapshot of the IoT IAM Market
5 Market Overview and Industry Trends
5.1 Introduction
5.2 Market Dynamics
5.2.1 Drivers
5.2.1.1 Rise in Adoption of BYOD Trend
5.2.1.2 Increase in Frequency of Cybersecurity Breaches and Cyberattacks
5.2.1.3 Increased Integration of IAM with IoT Devices
5.2.2 Restraints
5.2.2.1 Cost and Budget Concerns of IoT IAM Solutions
5.2.3 Opportunities
5.2.3.1 Adoption of Bring Your Own Identity (Byoi) Approach
5.2.3.2 Rise in Adoption of Biometric Technologies Through Smartphones, Laptops, and Tablets
5.2.3.3 Government and Private Sector Cyber Security Mandates
5.2.4 Challenges
5.2.4.1 Lack of Security, Expertise, and Awareness
5.3 Impact of COVID-19 on Market Dynamics
5.3.1 Drivers and Opportunities
5.3.2 Restraints and Challenges
5.3.3 Cumulative Growth Analysis
5.4 IoT IAM Market: Value Chain Analysis
5.5 Ecosystem
5.6 Pricing Model of IoT IAM Market Players
5.7 Technology Analysis
5.7.1 Introduction
5.7.2 Artificial Intelligence
5.7.3 Blockchain
5.7.4 Cloud Computing
5.7.5 Digital Twin
5.8 Case Study Analysis
5.8.1 Case Study 1: The Auto Club Group (Acg) Used Opentext Identity and Access Management Solution
5.8.2 Case Study 2: The City and County of San Francisco (Ccsf) Utilised Oracle'S IAM Solution
5.8.3 Case Study 3: Soti Works with Onelogin for Sso and Provisioning as It Moves to the Cloud
5.8.4 Case Study 4: Entrust Helps Banco Bice Comply with Sbif Security Regulations
5.8.5 Case Study 5: The City of Mesa Opted for Aspect Unified Ip Solutions from Alvaria to Offer Strong Interaction Choices
5.9 Revenue Shift for the IoT IAM Market
5.10 Patent Analysis
5.10.1 Methodology
5.10.2 Document Types of Patents
5.10.3 Innovation and Patent Applications
5.10.4 Top Applicants
5.11 Porter'S Five Forces Analysis
5.11.1 Threat of New Entrants
5.11.2 Threat of Substitutes
5.12 Regulatory Landscape
5.13 Key Stakeholders and Buying Criteria
5.13.1 Key Stakeholders in Buying Process
5.13.2 Buying Criteria
5.14 Key Conferences and Events in 2022-2023
6 Global IoT IAM Market, by Component
6.2 Introduction
6.2.1 Component: IoT IAM Market Drivers
6.2.2 Component: COVID-19 Impact
6.3 Solutions
6.3.1 Lifecycle Management
6.3.1.1 Provisioning
6.3.1.1.1 Increase in Security with Automated Provisioning
6.3.1.2 De-Provisioning
6.3.1.2.1 Vital Security Protocol That Ensures Protection of Data
6.3.2 Digital Certificate
6.3.2.1 to Perform Functions of Identification, Integrity, and Authentication
6.3.3 Api Management/Api Gateways
6.3.3.1 to Secure IoT Applications and Connected Devices
6.3.4 Authentication
6.3.4.1 Single Factor Authentication
6.3.4.1.1 Smart Passwords and Usernames for Single-Factor Authentication
6.3.4.2 Two Factor Authentication
6.3.4.2.1 Adoption of Two Factor Authentication for Better Protection
6.3.4.3 Multi Factor Authentications
6.3.4.3.1 Multiple Layers of Verification for Device Protection
6.3.5 Single Sign-On
6.3.5.1 Enterprise Sso
6.3.5.1.1 One-Click Access to All Enterprise Applications
6.3.5.2 Web and Federated Sso
6.3.5.2.1 Single Point of Access to All the Applications Across Different Organizations
6.3.6 Directory Services
6.3.6.1 Storage
6.3.6.1.1 Directory Server Offers a Central Source for Storing and Handling Information
6.3.6.2 Meta Directories
6.3.6.2.1 to Create a Consolidated View of Identity Information
6.3.6.3 Virtual Directories
6.3.6.3.1 Supports Various Protocols, Such as Ldap, Sql, Dsml, Spml
6.3.7 Access Management and Authorization
6.3.7.1 to Manage Multiple Identities Across Devices and Domains
6.3.8 Password Management
6.3.8.1 Self-Service Password Reset
6.3.8.1.1 Reset of the Password by User Securely
6.3.8.2 Password Reset
6.3.8.2.1 Create and Reset a New Password by Invalidating the Current Password
6.3.8.3 Password Synchronization
6.3.8.3.1 a Process of Accomplishing Single Sign-On (Sso)
6.3.9 Audit, Compliance, and Governance
6.3.9.1 Solutions Providing Comprehensive Support for Auditing
6.4 Services
6.4.1 Professional Services
6.4.1.1 Integration and Implementation
6.4.1.1.1 Implementation Services Facilitate the Integration of IoT IAM Solutions into Their IoT Infrastructure
6.4.1.2 Consulting
6.4.1.2.1 Advice and Knowledge to Clients on the Critical Issues
6.4.1.3 Support and Maintenance
6.4.1.3.1 Deployment of Advanced IAM Solutions to Secure Networking Devices
6.4.2 Managed Services
6.4.2.1 Outsourcing to Third-Party Service Providers to Manage Efficiently and Reduce Cost
7 Global IoT IAM Market, by Security Type
7.1 Introduction
7.1.1 Security Type: IoT IAM Market Drivers
7.1.2 Security Type: COVID-19 Impact
7.2 Network Security
7.2.1 Adoption of IAM Solutions to Enhance Network Security
7.3 Endpoint Security
7.3.1 Enhancing Endpoint Security with Authentication Solutions
7.4 Application Security
7.4.1 Adoption of IAM Solutions to Ensure Security
7.5 Cloud Security
7.5.1 Enhancing Cloud Security with IAM Solutions
7.6 Other Security Types
7.6.1 Boosting Database and Web Security with IAM Solutions
8 Global IoT IAM Market, by Deployment Type
8.1 Introduction
8.1.1 Deployment Type: Market Drivers
8.1.2 Deployment Type: COVID-19 Impact
8.2 Cloud
8.2.1 Easy Access to Computing Resources and It Services
8.3 On-Premises
8.3.1 On-Premises Solutions Opted for Critical User Credentials
9 Global IoT IAM Market, by Organization Size
9.1 Introduction
9.1.1 Organization Size: Market Drivers
9.1.2 Organization Size: COVID-19 Impact
9.2 SMEs
9.2.1 to Increase the Security of IoT Applications SMEs Opt for IAM Solutions
9.3 Large Enterprises
9.3.1 Large Enterprises Have Adopted IAM Solutions to Ensure Security
10 Global IoT IAM Market, by Vertical
10.1 Introduction
10.1.1 Vertical: Market Drivers
10.1.2 Vertical: COVID-19 Impact
10.2 Bfsi
10.2.1 Bfsi Industry to Choose IAM Solutions to Boost Security
10.3 Automotive
10.3.1 with Increasing Innovations in the Industry, There is a Need for IAM Solutions for Security
10.4 Telecom
10.4.1 Identity Solutions to Create a Seamless and Secure Customer Experience
10.5 It and Ites
10.5.1 It and Ites are Adopting IoT Solutions for Technological Innovations
10.6 Retail and Consumer Goods
10.6.1 Increase in Adoption of IAM Solutions to Protect Crucial Data from Hackers
10.7 Energy and Utilities
10.7.1 IAM Solutions to Eliminate Cyber Attacks
10.8 Healthcare
10.8.1 Security Solution to Preserve Privacy of Patients
10.9 Oil and Gas
10.9.1 with Rapid Technological Advancements, There is Adoption of Cyber Security Solutions
10.10 Manufacturing
10.10.1 Vast Industry Adopts Security Solutions to Enable Better Protection
10.11 Other Verticals (Education, Travel, and Hospitality)
10.11.1 Adoption of Identity Access Solutions to Enhance Security Across Verticals
11 IoT IAM Market, by Region
12 Competitive Landscape
12.1 Introduction
12.2 Key Player Strategies
12.3 Market Share Analysis of Top Players
12.4 Historical Revenue Analysis
12.5 Company Product Footprint Analysis
12.6 Market Ranking of Key Players in IoT IAM Market, 2022
12.7 Company Evaluation Quadrant
12.8 Startup/SME Evaluation Quadrant
12.9 Competitive Scenario
13 Company Profiles
13.1 Major Players
13.1.1 AWS
13.1.1.1 Business Overview
13.1.1.2 Products Offered
13.1.1.3 Recent Developments
13.1.1.4 Analyst's View
13.1.1.4.1 Key Strengths/Right to Win
13.1.1.4.2 Strategic Choices Made
13.1.1.4.3 Weaknesses and Competitive Threats
13.1.2 Thales
13.1.3 IBM
13.1.4 Microsoft
13.1.5 Broadcom
13.1.6 Opentext
13.1.7 Cisco Systems
13.1.8 Ericsson
13.1.9 Google
13.1.10 Micro Focus
13.1.11 Ping Identity
13.1.12 Oracle
13.1.13 Entrust
13.1.14 Hid Global
13.1.15 Digicert
13.1.16 Okta
13.1.17 Sailpoint
13.1.18 Dell EMC
13.1.19 Optiv Security
13.1.20 Cyberark
13.2 Startup/SMEs
13.2.1 Forgerock
13.2.2 One Identity
13.2.3 Verimatrix
13.2.4 Kaaiot
13.2.5 Identity Fusion
13.2.6 Keyfactor
13.2.7 Globalsign
13.2.8 Blue Ridge Networks
13.2.9 Sectigo
13.2.10 Fusionauth
14 Adjacent/Related Markets
15 Appendix
For more information about this report visit https://www.researchandmarkets.com/r/vqruas
Attachment
CONTACT: CONTACT: ResearchAndMarkets.com Laura Wood, Senior Press Manager press@researchandmarkets.com For E.S.T Office Hours Call 1-917-300-0470 For U.S./CAN Toll Free Call 1-800-526-8630 For GMT Office Hours Call +353-1-416-8900


 Yahoo Finance
Yahoo Finance 
