Teen phone tracking app leaked thousands of user details from unprotected servers
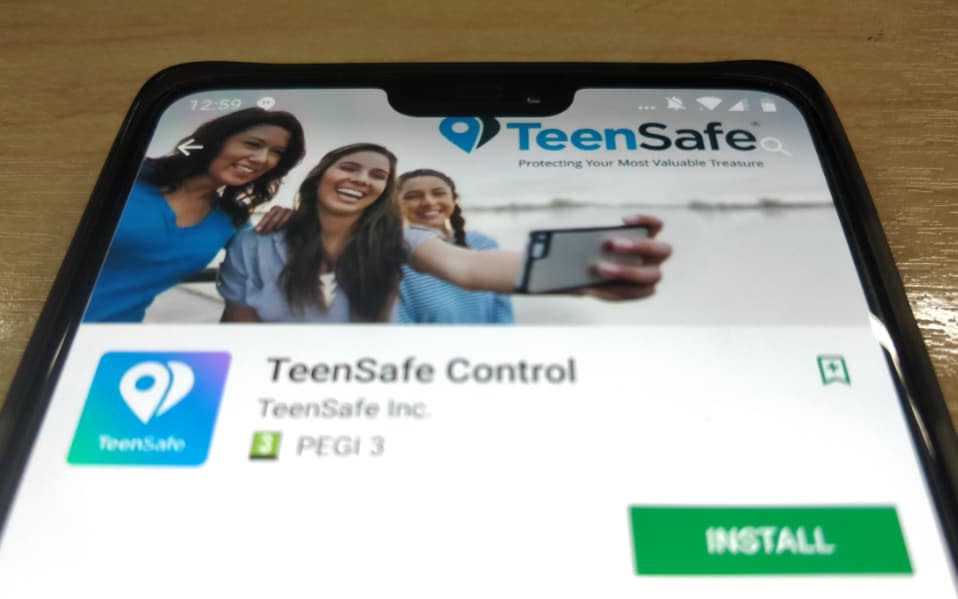
An app for parents to monitor their teenagers' smartphone activity has leaked tens of thousands of accounts of both parents and children from at least one unprotected server.
The mobile app, TeenSafe, that is available for iPhones and Android devices, claims to use "secure" tracking software that can be downloaded by parents onto their child’s smartphone.
It allows them access to their child's text messages, location, call log, the apps they install and their web browsing history.
However the Los Angeles-based company, which says it has over a million parents using its service, left some of its servers unprotected and accessible by anyone.
Robert Wiggins, a UK-based security researcher who found the two exposed servers that are hosted on Amazon's cloud, said as the server had no password this allowed users details to be easily obtainable, which could lead hackers to access children's Apple accounts.

The database stores the parent's email address associated with TeenSafe, as well as their corresponding child's Apple ID email address. It also includes the child's device name, which is usually just their name, and their device's unique identifier.
The data also contains the unencrypted passwords for the child's Apple ID. Because the app requires that two-factor authentication is turned off, which normally adds an extra layer of protection, a malicious actor viewing this data only needs to use the credentials to break into the child's account to access their personal data.
Both of the servers were taken offline after technology news site ZDNet reported the discover to the company, including another that contains what appears to be only test data.
"We have taken action to close one of our servers to the public and begun alerting customers that could potentially be impacted," said TeenSafe on Sunday.
ZDNet reported none of the records contained photos or messages, or the locations of either parents or children.
The data also contained error messages of failed account action, such as if a parent looking up a child's real-time location didn't complete.
Shortly before the server went offline, there were at least 10,200 records from the past three months containing customers data, but some are duplicates.
One of the servers appeared to store test data, but it's not known if there are other exposed servers with additional data. The company claims on its website that it's "secure" and uses encryption to scramble the data, such as in the event of a data breach.

 Yahoo Finance
Yahoo Finance 